Community West Bank
Services we provide:
- Discovery
- Strategy
- UX/UI design
- Website development
- Xperience by Kentico implementation
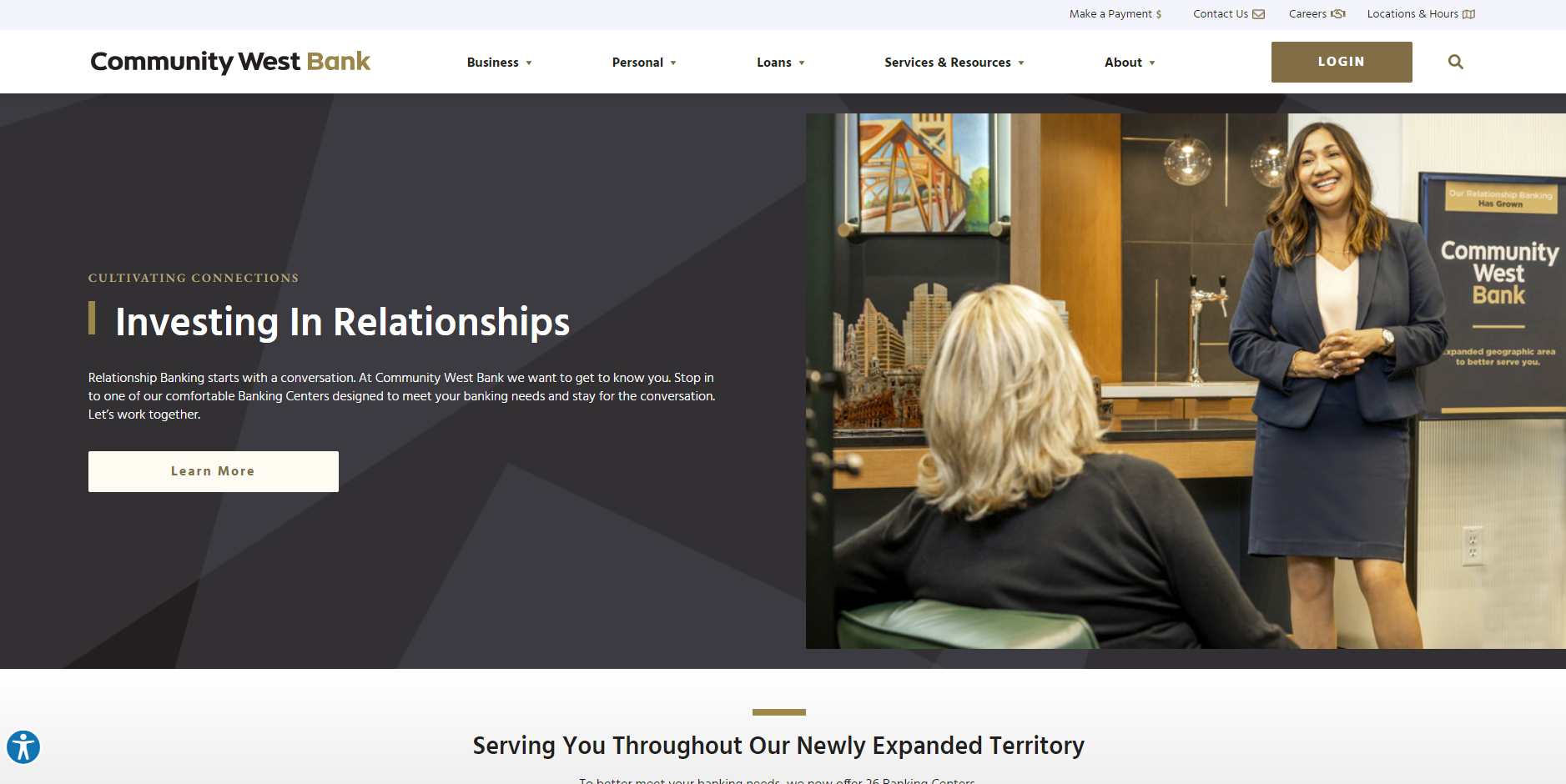
About Community West Bank
CWB is a large community bank in southern California with over 20+ locations and a track record of financial strength, security and stability gained over its 44 years in business. CWB has set itself apart from other banks by its people, dedication to client advocacy, exemplary "relationship banking," strong community support and a mission to exceed expectations. With a passion for providing customized solutions, the merger drove the decision to revamp their digital services to better serve their customers.
The Process
In an era where digital presence is critical to financial institutions and mergers are frequent, the successful merger of Community West Bank (CWB) and Central Valley Bank (CVB) depended on a robust and well-executed digital strategy, critical to providing a seamless user experience for customers and employees. SilverTech, leveraging its expertise in Xperience by Kentico website development, customized a digital solution that unified the brands of these two banks into one cohesive user-friendly digital experience in just 4 months from start to launch.
The Challenges
The merger of CWB and CVB presented unique challenges, particularly in integrating two distinct digital landscapes into a single cohesive website. The biggest challenges included:
- Differing Content Strategies: CWB's site was optimized for SEO with a rich content library, while CVB's site focused more on detailed product pages. Balancing these different content approaches was crucial.
- Short Timeline: The project needed to be completed with a demanding timeline, delivering a high-quality, functional website, from planning to launch in less than four months.
- Outdated Technology: The old CWB site suffered from poor mobile optimization, slow speeds, outdated information, and a lack of interactive features. This hindered customer engagement and usability.
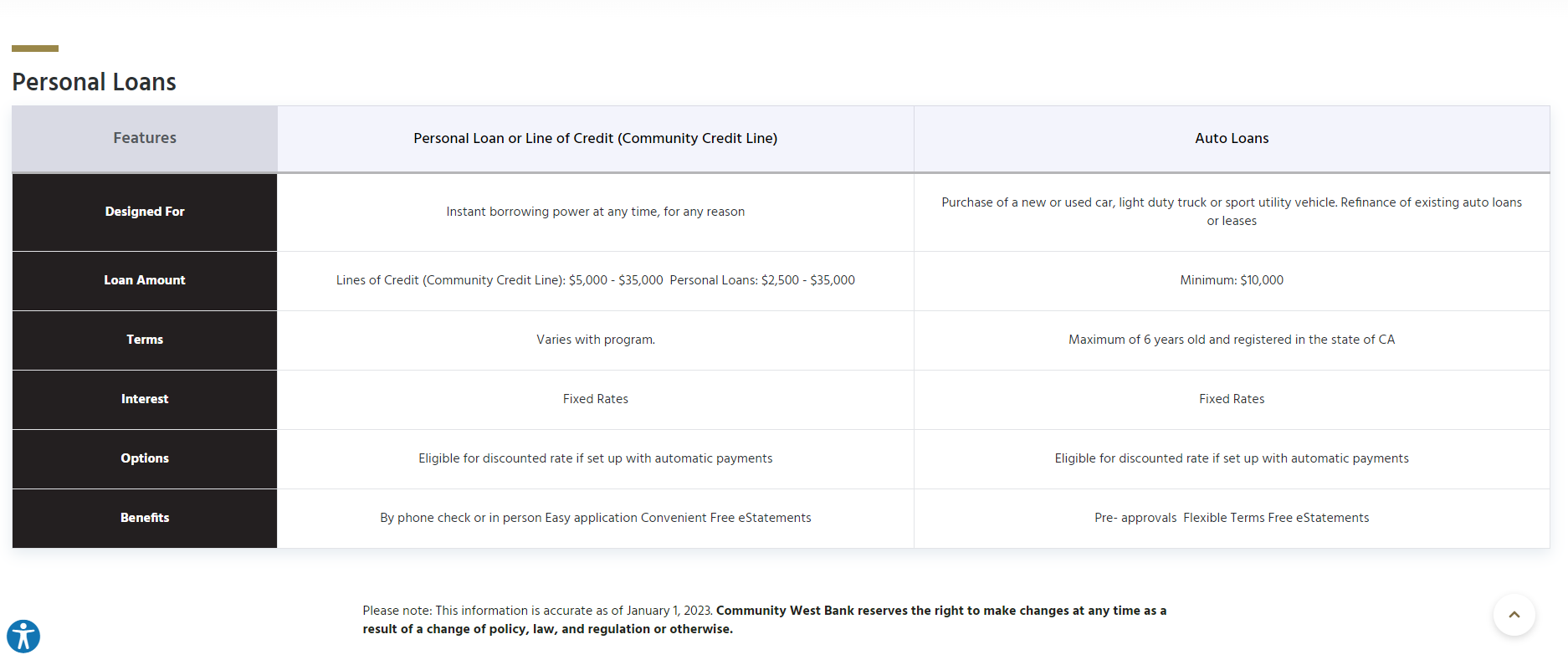
Goals for New Site
SilverTech identified four main goals for CWB's new website with the main goal of unifying the brands. The merger of the two banks presented a unique opportunity to take advantage of the best from both brands.
Solution and Implementation
Based on the insight gained, SilverTech devised a comprehensive strategy roadmap to address the challenges and deliver a seamless digital experience for the bank merger. It was SilverTech's recommendation that Kentico's newest hybrid CMS platform Xperience by Kentico would be the best solution for the new website. Xperience with robust features and functionality allowed SilverTech to create an exceptional digital user experience efficiently for CWB.
The Key components of the solution include:
- Unified Content Strategy: SilverTech developed a content migration plan that combined the SEO-rich content from CWB with the detailed product information from CVB. This approach ensured that the new site would benefit from both banks' strengths while avoiding duplication and inconsistencies.
- Modern Design and Functionality: The new website was built with Xperience by Kentico, featuring a modern, responsive design to enhance user experience across all devices. Key features included:
- Enhanced Interactivity: Interactive elements and engaging content to improve customer interaction and retention
- Improved CTAs: Clear, strategically placed CTAs to guide users through the site effectively
- Technical Upgrades: Faster loading speeds, improved reliability, and mobile optimization to ensure a smooth user experience
- New Functionalities: Inclusion of essential tools like product comparison tools, branch locator and more
- Accelerated Development Timeline: Despite the tight timeline, SilverTech employed agile development practices to ensure timely delivery without compromising quality. The team worked in sprints to continuously test and refine the site, leading up to a successful launch within the four-month timeframe.
HIGHLIGHTS
The Ultimate Guide to New Digital Terms You Need to Know
12/3/24
With digital transformation evolving at lightning speed, it brings a host of new technologies and jargon that shape how businesses operate. Understanding these terms is essential for anyone navigating the digital world. This guide covers some of the latest digital terms and acronyms, with a focus on data management, security, and cutting-edge technologies like AI and machine learning.
Customer Data Platform (CDP)
A Customer Data Platform (CDP) is a centralized system that collects, organizes, and manages customer data from various sources like websites, emails, and social media. It unifies this data to create a comprehensive customer profile that businesses can use to personalize marketing efforts and improve customer experience. Unlike a traditional data management platform (DMP), a CDP is designed to provide a persistent, unified customer database that is accessible to other systems. The goal is to enhance personalized marketing efforts by enabling a deeper understanding of customer behavior.
- Example: A retail company using a CDP can gather data from its e-commerce website, mobile app, and social media to create a single customer profile, allowing for more targeted promotions and improved customer engagement.
Digital Asset Management (DAM)
A Digital Asset Management (DAM) system is a centralized repository for storing, organizing, and managing an organization’s digital assets. These assets can include images, videos, audio files, documents, and other multimedia content. DAM solutions make it easier for teams to find, share, and use digital content efficiently across departments while maintaining control over asset versions and permissions, streamlining workflows and ensuring brand consistency.
- Example: A marketing team can use a DAM platform to store branding materials, ensuring all team members have access to the most up-to-date logos, brochures, and advertisements. Ensuring that all assets comply with the brand guidelines.
Product Information Management (PIM)
Product Information Management (PIM) is a platform or software solution that helps businesses manage and centralize product data. It ensures consistent, accurate, and up-to-date product descriptions, specifications, pricing, and images, ensuring consistency across all sales channels, like e-commerce websites, catalogs, and brick-and-mortar stores.
- Example: A company that sells electronics could use a PIM system to manage product specifications for smartphones, ensuring that every online retailer displays consistent product descriptions and accurate details.
Software as a Service (SaaS)
Software as a Service (SaaS) refers to cloud-based software solutions that are hosted by a third party and delivered over the internet. Instead of purchasing and installing software outright, users typically pay a subscription fee for access to SaaS products, which are often updated and maintained by the service provider. SaaS is popular for its scalability, accessibility, and cost-effectiveness.
- Example: Applications like Google Workspace, Salesforce, and Microsoft 365 are all SaaS applications, enabling users to access tools for communication, collaboration, data storage, customer relationship management and productivity from anywhere with an internet connection.
AI (Artificial Intelligence)
Artificial Intelligence (AI) refers to the simulation of human intelligence in machines. AI systems can perform tasks that typically require human intelligence, such as recognizing patterns, understanding natural language, making decisions, and solving complex problems.
- Example: AI chatbots on customer service websites provide real-time assistance by answering customer queries, without the need for human intervention.
ML (Machine Learning)
Machine Learning (ML) is a subset of AI that enables computers to learn from data without being explicitly programmed. ML algorithms analyze large datasets, identify patterns, and improve decision-making over time, making predictions or decisions based on historical data.
- Example: E-commerce platforms use ML algorithms to recommend products based on a customer’s past browsing and purchasing behavior.
Zero Trust Security Model
The Zero Trust Security Model is a cybersecurity model that operates on the principle that no user, inside or outside of the organization, should be trusted by default. is a security framework that operates on the principle of "never trust, always verify." In this model, no one is trusted by default—whether inside or outside the organization's network. Every user or device must be authenticated, authorized, and continuously validated before being granted access to any resource.
- Example: A company implementing Zero Trust requires all employees to authenticate their identities before accessing the internal network, even if they are on-site or using a company device.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a security measure that requires users to provide two or more verification factors to gain access to a system or application. These factors typically include something the user knows (password), something the user has (a physical token or smartphone), and something the user is (biometric verification, such as a fingerprint or face recognition).
- Example: When logging into an online bank account, a customer may need to enter their password (something they know) and confirm their identity via a code sent to their smartphone (something they have).
DLP (Data Loss Prevention)
Data Loss Prevention (DLP) refers to a set of tools and processes used to ensure that sensitive data is not lost, misused, or accessed by unauthorized users. DLP systems monitor, detect, and block unauthorized attempts to transfer data outside of an organization’s control.
- Example: A company implements DLP to prevent employees from accidentally sending confidential data via email to unauthorized recipients.
SOC (Security Operations Center)
A Security Operations Center (SOC) is a centralized unit within an organization that deals with security issues on a technical level. The SOC team monitors and analyzes network traffic and systems for signs of malicious activity or security breaches.
- Example: The SOC at a large corporation continuously monitors their IT infrastructure for any signs of suspicious activity and swiftly responds to potential threats.
Blockchain
Blockchain is a decentralized, distributed ledger technology that records transactions across multiple computers in such a way that the transactions are immutable and transparent. It is often associated with cryptocurrencies like Bitcoin, but its uses extend to supply chain management, voting systems, and more.
- Example: A shipping company uses blockchain technology to track the movement of goods across the supply chain, ensuring transparency and authenticity at every stage.
IoT (Internet of Things)
The Internet of Things (IoT) refers to the network of physical devices—ranging from household appliances to industrial machines—that are connected to the internet and can collect and exchange data. IoT technology allows these devices to communicate and perform actions autonomously or be controlled remotely.
- Example: Smart thermostats, home security cameras, and wearable fitness trackers are common IoT devices that collect data and can be controlled through mobile apps.
RPA (Robotic Process Automation)
Robotic Process Automation (RPA) is a technology that uses software robots, or "bots," to automate repetitive, rule-based tasks typically performed by humans. RPA is widely used to streamline processes in industries like banking, insurance, and manufacturing.
- Example: A bank uses RPA to automate the processing of loan applications, reducing the need for human intervention and speeding up approval times.
BYOD (Bring Your Own Device)
Bring Your Own Device (BYOD) is a policy that allows employees to use their personal devices, such as smartphones and laptops, to access company systems and data. While it can improve flexibility and productivity, BYOD also introduces security risks that need to be managed.
- Example: An organization adopts a BYOD policy, allowing employees to access work emails and documents from their own smartphones, but implements strict security protocols to protect sensitive data.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems are tools that collect, analyze, and store data related to security events in real-time. SIEM helps organizations detect, respond to, and mitigate potential security threats by correlating information from various sources, including network devices, servers, and applications.
- Example: An enterprise using a SIEM platform can monitor abnormal user behavior, such as multiple failed login attempts, to detect and respond to potential security breaches more quickly.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a cybersecurity solution that monitors and responds to threats on endpoint devices, such as laptops, desktops, and mobile devices. EDR tools detect suspicious activities, provide real-time alerts, and enable the remediation of cyberattacks targeting endpoints.
- Example: A company deploying EDR software can identify malware on an employee’s laptop and quarantine the affected files to prevent further spread across the network.
These terms represent the forefront of technological innovation and digital security. By keeping up with these digital terms, businesses and individuals can better understand how to leverage technology to improve operations, enhance security, and streamline workflows. Understanding these terms also empowers you to adapt to the evolving digital landscape in both personal and professional contexts. Whether you're in marketing, IT, or management, these technologies play an essential role in shaping the digital strategies of modern organizations.